Cybersecurity is a team sport, as malicious actors and advanced persistent threats are constantly evolving their tactics. In this ever-changing landscape, it is crucial for organizations to collaborate and learn from one another’s experiences. At Devo, we recognize the importance of teamwork in combating these threats. We are committed to enhancing our product capabilities and content to empower every customer to participate in this collective defense.
Introducing Devo Collective Defense
Analysts often bear the burden of understanding the significance of isolated incidents within the ever-evolving threat landscape. They need a threat intelligence solution that provides timely threat context so they can take action with decisive confidence.
Though threat intelligence has had a longstanding history, collaborative contributions to these datasets have remained scarce, leading to a unidirectional flow of information to end users. Traditional SIEMs have faced limitations in intelligence sharing because they operate on private, on-premises networks. Even with cloud migration through lift and shift approaches, modern SIEM architectures have struggled to support effective information sharing across the user community.
At Devo, we have changed that paradigm and doubled down on our commitment to accelerating analyst decision making, fostering collaboration, and collective strength. We are pleased to announce Devo Collective Defense, a community-based intelligence-sharing program that provides knowledge of threat activity and trends exclusively to Devo customers’ and partners’ security teams.
The Devo Platform provides modern enterprises complete visibility into threats across all customer environments with its strategic location within the cloud, which enables Collective Defense to analyze millions of data points across thousands of domains with strict privacy controls, giving security teams the ability to expedite triage and accelerate investigations while strengthening the Devo user community.
Devo Collective Defense helps customers detect emerging threats.
Devo Collective Defense helps customers detect emerging threats.
How Does Collective Defense Work?
Collective Defense automatically aggregates alerts, investigations, and contained threats across the Devo user community. It provides users with a unique combination of up-to-date threat intelligence and pre-built content that helps security teams make data-driven decisions to effectively investigate threats and respond to attacks.
Collective Defense gives Devo customers exclusive access to:
- Threat Intelligence Feed – The Collective Defense threat intelligence feed contains emerging threat details seen across the Devo community and can be used to add context to alerts, Activeboards, and query results.
- Threat Hunting Alert Packs – A set of alerts for Devo’s most popular ingested log sources such as AWS, Office365, Windows, and firewall. Collective Defense alerts detect malicious IOCs and elevates risky entities across the organization.
- Intelligence Visualizations – Collective Defense Activeboards visually display insights, patterns, threat hits, and trends so analysts can quickly identify suspicious behavior.
- Alert Enrichments – A new multi-lookup that enables analysts to correlate entity data, such as IP, domain, and URL against the Collective Defense feed to identify complex attacks.
Collective Defense Activeboards display insights so analysts can quickly identify anomalous behavior.
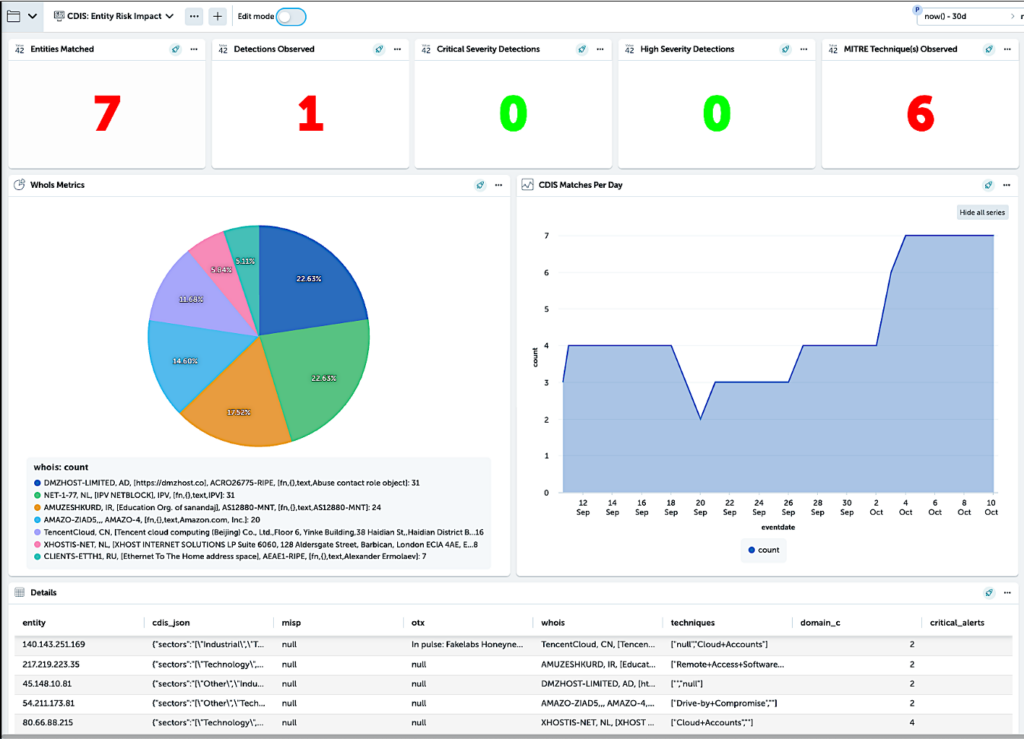
Collective Defense Activeboards display insights so analysts can quickly identify anomalous behavior.
Updates to Devo Exchange and the MITRE ATT&CK Adviser
Devo Exchange
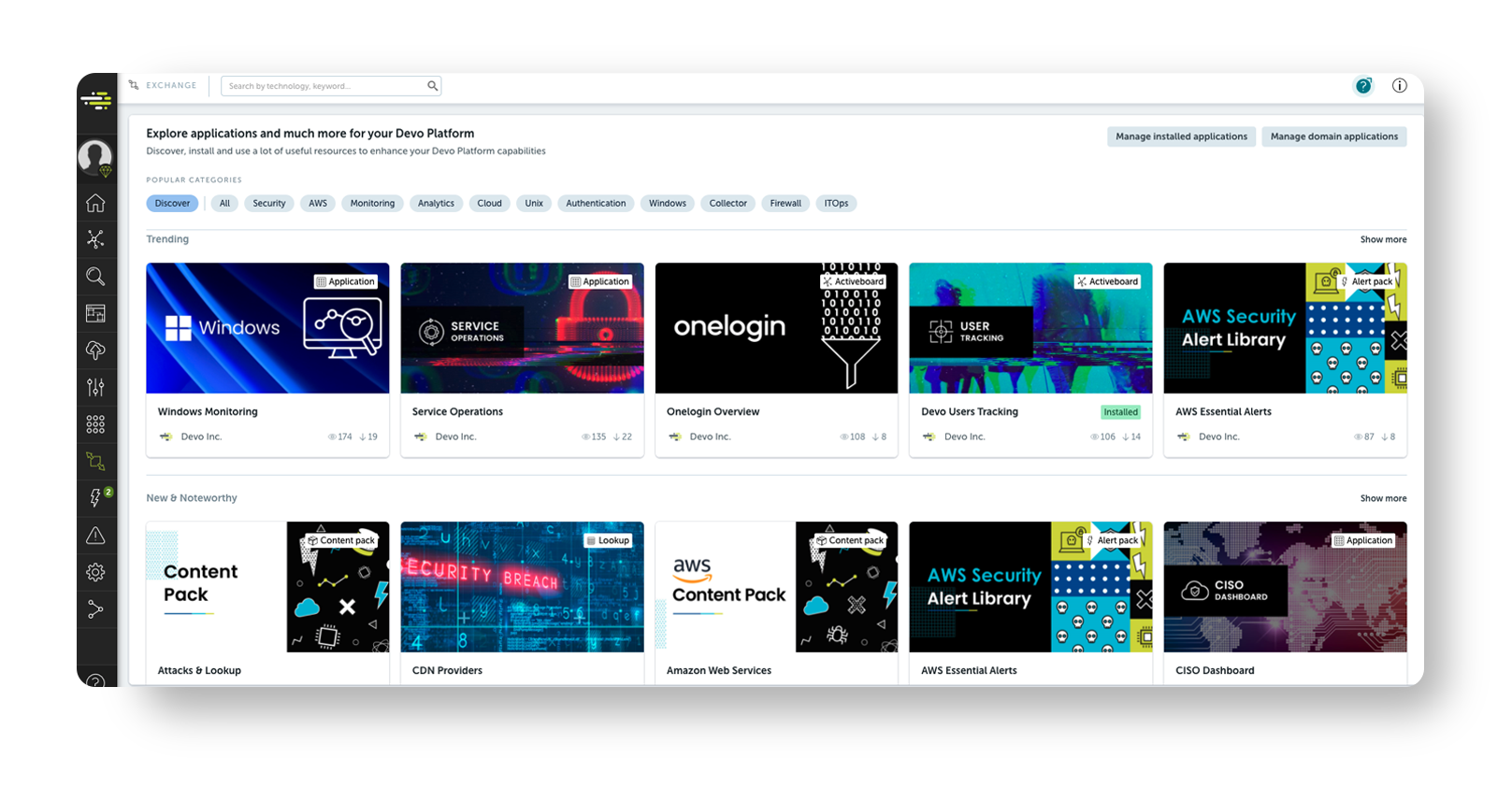
Devo Exchange is the community-based marketplace in the Devo Platform that extends security teams’ capabilities by providing them with on-demand access to a catalog of Devo-curated content created by Devo, its partners, and the greater security community.
Devo Exchange continues to provide new, curated content for the Devo community. Users now have access to over 200 pieces of downloadable threat content packs and applications. This includes over 524 alerts covering the MITRE ATT&CK framework, firewalls, proxy servers, AWS, and Azure.
Additional Devo Exchange content includes:
- Activeboards for Azure, Office365 and AD Overview, Proxy Zscaler Activity
- Technology packs containing over 300 out-of-the-box alerts covering an array of common technologies such as Google Cloud, G-Suite, MS Windows, Office365, and Linux.
Devo Exchange also now provides technology packs that are tailored for the key data sources that users ingest into the platform, including Office365, GCP, Azure, Firewall, Proxy, G-Suite, Linux, and AWS. These alerts packs enable analysts to quickly install and configure alerts to protect their organization after onboarding their data sources to Devo, saving them hours of searching and analysis time.
Users have access to over 200 pieces of downloadable threat content packs and applications.
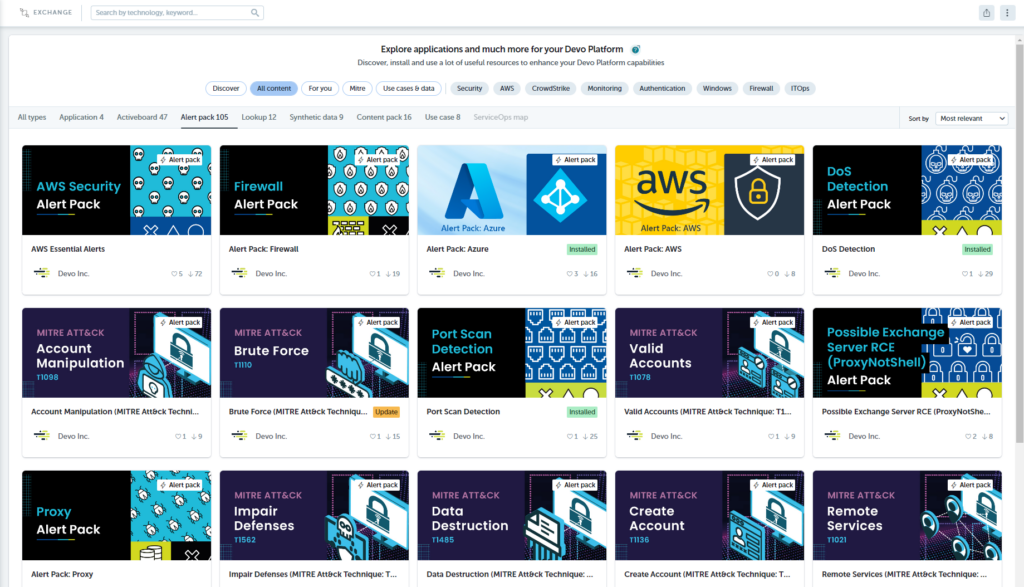
Users have access to over 200 pieces of downloadable threat content packs and applications.
Devo MITRE ATT&CK Adviser
The Devo MITRE ATT&CK Adviser application maps alerts and log sources to MITRE ATT&CK tactics and techniques via alert heatmaps, alert coverage maps, and log source coverage maps. We have expanded its capabilities to increase organization visibility and customization.
New feature improvements:
- Application Configuration – The adviser application provides a configuration section that enables users to specify whether certain alerts, techniques, or log sources are relevant to each environment, increasing coverage score accuracy.
- Multi-domain filters – If data is segmented into multiple domains or you’re an MSSP, the multi-domain filter gives organizations visibility into coverage in all domains from a single screen.
- Improved Export – Identifying coverage gaps to improve can involve teamwork. All coverage data can be exported for team discussions on improvements.
Configure the MITRE ATT&CK Adviser app to filter specific alerts, techniques, and log sources.
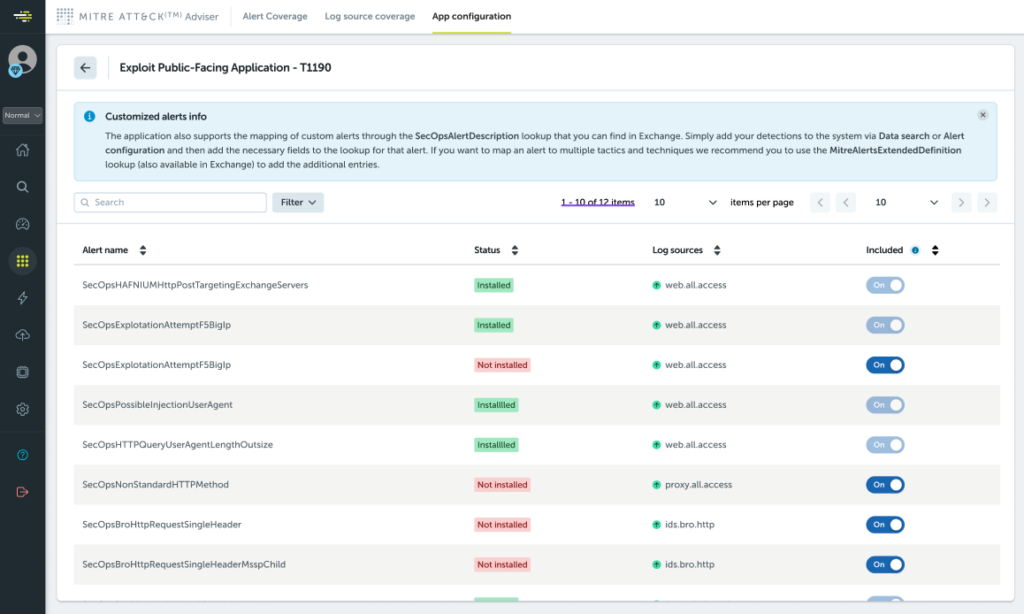
Configure the MITRE ATT&CK Adviser app to filter specific alerts, techniques, and log sources.
Better Collaboration Enables a Stronger Defense
The convergence of Collective Defense’s expansive threat intelligence, Devo Exchange’s invaluable content resources, and the enhanced capabilities of the Devo MITRE ATT&CK Adviser constitutes a powerful synergy that bolsters the strength of the Devo community. Here at Devo, we are thrilled to offer our customers an unrivaled opportunity to elevate their analysts’ expertise and bring their operational efficiency to new heights.
Want to learn more?
Please refer to the Devo Documentation for the latest features in Devo Collective Defense, Devo Exchange, and the Devo MITRE ATT&CK Adviser.
Want to learn more about how our customers are using collaborative intelligence to improve their cybersecurity defenses? Talk to our product experts and your security peers at Devo Connect, our online user community.