
eBook Journey to the Autonomous SOC
Unlock the power of automation. Discover the key factors for automating threat detection, hunting, and response in this ebook.
According to the Identity Theft Resource Center’s 2021 Data Breach Report, there were over 1,800 breaches in 2021, exceeding the previous all-time high record of 2017 by 23%. Knowing such realities, modern organizations can’t rely solely on legacy tools to protect their IT network. Rather, they need a more proactive way to detect and remove cyber threats and keep the bad actors out. Here’s where threat hunting comes in. Threat hunting enables cybersecurity teams to actively find and remove threats before they can damage the enterprise network. . Moreover, legacy, signature-based detection tools often miss these threats, so with threat hunting, organizations get a more comprehensive and proactive way to detect and remove threats early.
Effective threat hunting requires skilled personnel armed with robust threat hunting tools. But considering the sheer number of tools that are now available, finding the right one can be a challenge for many organizations. This article aims to minimize this challenge, helping you identify the most suitable tool for your threat hunting requirements.
| Feature | Description |
|---|---|
| Data collection | Centralized data management to provide full visibility into the network, devices/endpoints, and applications; on premise and cloud |
| Security Analytics | Help develop threat models based on threat intelligence and detect advanced threats |
| Behavior Analytics, Machine Learning, and Artificial Intelligence | Detect and flag anomalies that may indicate a threat behavior that rule-based security solutions often miss |
| Security monitoring | Collect security data from a wide range of sources to detect and respond to possible threats and breaches on the network, endpoints, and cloud infrastructure |
| Threat Intelligence | Evidence-based data from multiple internal or external sources. External sources include social media, the dark web, and press releases. Internal sources could include evidence observed/collected from previous attacks or honeypots. |
| Malware analysis | Analyze malware samples, “reverse engineer” these samples to pull out suspicious IoCs like hashes or strings, and run the malware to understand its propagation capabilities and threat profile |
Threat hunting tools proactively search for cybersecurity threats that may bypass traditional security solutions like firewalls or antivirus software. With these tools, threat hunters can identify abnormal or malicious behavior, and reduce dwell time intrusions by bad actors that may lead to data theft or damage to the enterprise.
Each threat hunting tool has different capabilities that look for different forms of threat. For instance, some capabilities find suspicious Indicators of Compromise (IoC) and Indicators of Attack (IoA) that may indicate the presence of malware threats. Others stop phishing attempts in real-time and prevent bad actors from exfiltrating sensitive data. Some tools help hunters create “hypotheses” to identify behaviors that indicate threat actors are attacking the network – something that signature-based tools often miss.
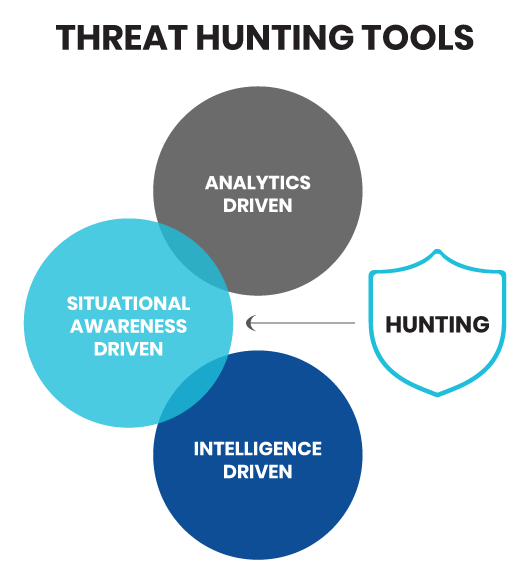
Most threat hunting tools fall into one of three categories (Source)
In general, most tools fall into one of three categories:
These tools collect, aggregate, and analyze threat intelligence and apply it against threat hunting logic. These tools use IOCs and pattern matching from threat intelligence to discover threats such as malware and ransomware within the environment.
Some tools can also raise alerts if phishing emails enter the enterprise perimeter. Others compile intelligence from public sources to filter spam email, prevent server abuse, and keep dangerous bots out of the network.
Analytics-driven tools leverage machine learning and behavioral analytics to mine large quantities of security data from different sources. They understand adversaries’ tactics, techniques and procedures (TTPs) to help hunters formulate threat hunting hypotheses, to identify indicators of attack (IoA). They also correlate data to identify suspicious behavior patterns that may indicate a threat, and provide deep, actionable insights that help accelerate threat hunting and forensic investigation.
These tools use AI to identify risk that allows hunters to create relevant threat hunting hypotheses based on the organization’s requirements, environment, and its IoCs and IoAs. They may also perform crown jewel analysis (CJA) so hunters can:
The following are key features of any good threat hunting solution that you might be considering:
Data logs are a basic requirement of any security administration software. The tool should provide system and operating system event logs, and logs from the network, endpoints, and applications to provide visibility into the network and any anomalous activities. It should also provide endpoint logs and device telemetry data, including:
Security Information and Event Management (SIEM) tools enable security teams to gather and analyze events and log data from multiple sources in a centralized platform. These tools provide enterprise-wide visibility and raise real-time alerts if they detect suspicious activity or threats. Security personnel can then analyze the results to identify malicious actors and put into place appropriate countermeasures. Thus, although SIEM is not necessarily a part of the threat hunting tool itself, it does provide a useful addition to the threat hunting ecosystem.
Security analytics offers much deeper insights into security data, which helps accelerate threat hunting. Security Analytics moves away from rule-based approaches and focuses on data statistics and patterns. Thus, they enable threat hunters to detect even advanced threats and attacks for which the attacker or attack signature are unknown.
For example, sophisticated attackers could use command and control (C&C) servers and unknown malware that are not present on any threat feed. Security Analytics can identify such advanced malware with “beaconing patterns” and C&C servers. In this way, threat hunters can detect the previously unknown attack and act quickly to mitigate damage.
Security Analytics can also detect infected hosts where the file pattern and URL are both unknown. They do this by identifying any outliers in URL access data based on the number and frequency of accesses in a certain previous period (e.g., a week) and then generating a list of potentially compromised hosts. Security analytics is also crucial to detect new data leakage scenarios that traditional data loss prevention (DLP) solutions miss. Traditional solutions can detect leakage only if the data patterns are known, but not leakages beyond known data or when communication is encrypted. Here’s where security analytics come in. Thus, like SIEM, analytics tools are a crucial component of the threat hunter’s arsenal.
Advanced threat hunting tools with advanced analytics capabilities can spot anomalous user behavior and reveal IoAs, which are often harder to detect than IoCs. They can also reveal hidden threats, enabling security teams to isolate them and prevent attacks. You can learn more by reading our article on security analytics .
AI or machine learning-driven can automatically analyze large sets of related data to isolate similar anomalous data characteristics between system and network activities. These tools create threat baselines and “learn” from data to update the baselines and improve their capabilities over time. This approach can also have a predictive nature. They thus enable threat hunters to keep pace with the changing TTPs of cybercriminals. Common use cases for these new-age tools include:
Threat intelligence is evidence-based data collected from internal or external sources. The Open Source Intelligence (OSINT) framework provides a list and mapping of free public sources such as social media, dark web, newspaper articles and press releases. Threat intelligence enables more proactive threat hunting when compared to typical security data, since it is contextualized and evidence-based. With up-to-date threat intelligence, organizations can better understand threats, place them into context and make informed decisions which enable building robust security mechanisms that neutralize them and protect assets.
Furthermore, hunters can leverage threat intelligence to understand a threat actor’s motives, targets, and attack behaviors in order to uncover hidden threats and preempt future attacks. By correlating collected intelligence with information like email addresses and IP addresses, they can contextualize suspicious activity to improve situational awareness and help them with deeper and more detailed investigations.
Some threat hunting tools centralize and aggregate information about IoCs and TTPs that might indicate a malware attack. Advanced tools can even provide a sandboxed environment where malware can be safely reverse-engineered. This allows security administrators to gain a greater understanding of its threat profile and stop it before it can damage the environment.
To provide a few practical examples, we have listed some popular threat hunting tools below:
| Tool name | Key features/USP |
| Devo (with Kognos) | cloud-native logging, security analytics and SIEM platform to simplify security operations, increase observability of the expanding threat landscape and defend against existing and evolving threats enabling autonomous threat hunting and triage |
| Phishing Catcher | detects suspicious phishing domains in near real-time |
| DNSTwist | detects suspicious domains, live phishing pages and domains configured to, or perform, reconnaissance on enterprise networks |
| YARA | allows threat hunters to identify and classify malware samples and create descriptions of malware families for more reliable detection |
| Automater | analyzes URLs, domains, IP addresses and Md5 hashes from multiple sources to simplify intrusion analysis |
| BotScout | tracks the IP address, name and email addresses of bots to prevent spam, server abuse, and database pollution and protect online assets |
Reliable threat hunting requires both advanced tools and the experienced cybersecurity professionals to use them. These experts should apply these tools based on the organization’s specific needs and using an appropriate threat hunting methodology whether that is IoC-based (structured) or hypothesis-based (unstructured).
These methods are all types of unstructured, or hypothesis driven, threat hunting. This approach starts with a hypothesis that may be based on IoAs and an attacker’s TTPs. The latter is often derived from threat intelligence sources like the MITRE ATT&CK framework. Using IoAs and TTPs, threat hunters can identify threats and threat actors in the early stages of an attack before they cause much harm.
On the other hand, structured threat hunting starts with an IoC. The IoC may contain a known maliciou destination or hash indicating malicious software which the hunter uses to search data in their environment. This example often leads the hunter to a hypothesis driven method where the hunter searches the network for malicious patterns before and after the IoC is triggered. The approach can help them discover new threats or threats that penetrated the environment in the past.
Threat hunting is not about selecting one type of tool “because it’s better” than the others. Rather, it’s about selecting the right tool or set of tools to suit the firm’s business case, risk priorities, and cybersecurity capabilities.
Many such tools are actually open-source, freely available, and fairly capable. However, paid tools are generally more effective and feature-rich out-of-the-box, but typically incur licensing fees that can add up over time. All threat hunting tools have their own purpose and area of focus. Some thwart phishing attempts, while others like Devo provide advanced analytic capabilities that can streamline security operations and minimize attack surface. Many tools can also be used in combination to provide even greater visibility and defense-in-depth against various cyberattacks and threat actors.
It’s also a good idea to note any overlapping features or capabilities between tools, to minimize unnecessary rework, leverage synergies and optimize the effectiveness of your threat hunting ecosystem. Make sure the tools you select can help hunters identify potential threats such as unauthorized devices, malicious activity, and flag IoCs for further analysis and action to help prevent threats and reduce threat actor dwell time.
First though, ensure that these tools have the data they need to effectively assess and address threats. Create a “baseline” for normal operations or activities. This provides threat hunting platforms with the contextual knowledge required for more effective discovery. Finally and if possible, deploy intelligence-driven tools into a formal Security Operations Center (SOC), staffed with skilled and knowledgeable analysts.
To beat bad actors, you need powerful weapons in your cybersecurity arsenal. This includes threat hunting tools. Used correctly, they can help uncover adversarial activity and destroy threats quickly and efficiently. So, make sure to invest time and effort in selecting and implementing the most appropriate tools for your enterprise. We hope that in some small way, this article will have helped you in your cybersecurity journey.