
IDC FutureScape 2023
In IDC FutureScape: Worldwide Future of Trust 2023 Predictions forecasts that by 2026, 30% of large enterprise organizations will migrate to autonomous security operations centers.
According to the 2022 Cyber Security Report, the number of cyberattacks against organizations increased by 50% in 2021 compared to 2020. Most cybercriminals that attacked companies were looking for intellectual property, login credentials, personal data or trade secrets. A further study by Positive Technologies found that they successfully penetrated 93% of enterprise networks, and used dangerous malware in 63% of attacks.
To stay ahead of these threats and to protect assets from determined cybercriminals, organizations need more proactive and preemptive cybersecurity. Specifically, they need threat detection and response (TDR).
TDR is the ongoing process of quickly detecting, investigating and responding to cyberthreats to minimize damage. A robust TDR program will help protect organizations from various threats including malware and ransomware, botnets, phishing, social engineering, DDoS attacks, and credential compromise.
This comprehensive guide will explore the benefits of TDR as well as the key components, tools, and best practices required to make implementation successful.
Here are some of the most important features of TDR tools. These are explored in further detail in a later section.
| Feature | Description |
|---|---|
| Malware detection and analysis | AI- and sandbox-based tools to identify sophisticated malware that can evade traditional security tools |
| Real-time visibility into the attack surface | Tools to provide full visibility into the entire attack surface |
| High-quality alerts and automated threat remediation | Fewer false positives to reduce the burden of analysis and automated workflows to speed up remediation |
| Support for threat hunting and analysis | Access to vital data to enable ongoing threat hunting and analysis |
Rapid digitization, cloud computing and remote working make the enterprise network more complex and increasingly vulnerable to threats. These threats can come from anywhere and attack any device or application on any network. Recently, adversaries have become even more sophisticated and are able to conduct stealthy attacks that evade traditional cybersecurity tools.
In such a complex and high-risk landscape, security teams are not always able to respond effectively against every form of threat or attack, particularly when working with traditional tools. Instead, they need more advanced systems that provide high-quality alerts, timely threat data, and automated response workflows. In short, they need TDR. Well implemented TDR programs will leverage multiple cutting-edge tools and techniques, including:
Used together, these tools enable threat hunters to proactively detect threats, stop attacks early, and reduce the risk to business. Hunters and tools should work in tandem to identify and investigate suspicious events, and respond appropriately to neutralize them. TDR forms a strong line of defense in a multi-layered cybersecurity system — exactly what today’s organizations desperately need.
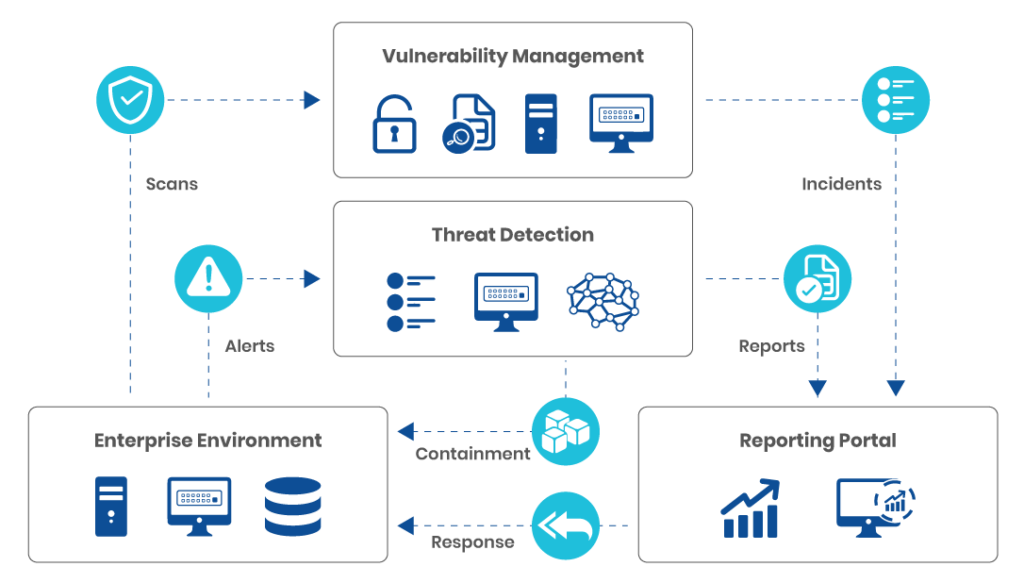
A example flow for threat detection and response (Source)
A robust TDR program consists of five key components that enable threat hunters to uncover, investigate, and mitigate against most threats and adversaries:
Robust prevention technologies enable security teams to proactively discover threats that could otherwise cause extreme damage. These solutions also dramatically reduce false positives, so personnel can focus on the threat signals that truly matter. Free from distractions, security teams can now take steps to strengthen existing defenses and protect business-critical systems and data.
Cybersecurity teams need timely access to information from many sources. This is to ensure accurate and reliable threat hunting and analyses. All collected data must be of the right type, volume and quality in order to successfully identify indicators of attack and to implement appropriate preventive measures.
Many security tools restrict themselves to only raising alerts about malicious activities or threats. But they do not act on these alerts or differentiate between actual threats and false positives. This results in large alert volumes that burden security analysts and make it harder to identify real threats.
To ensure that all critical events are addressed appropriately, alerts must be properly assessed and prioritized. This is where SOAR and AI-based TDR automated workflows become particularly useful.
After alerts are prioritized, they must be investigated to understand if a threat truly exists. It can be useful to compare these key signals against well-known threat investigation frameworks like MITRE ATT&CK and models such as Lockheed Martin’s Cyber Kill Chain.
These models and frameworks provide guidance for threat analysts and hunters to better understand an adversary’s tactics, techniques and procedures (TTPs). They also help identify how an adversary may attack the organization, and whether signal activity indicates a genuine attack. This information enables security to conduct more proactive threat hunting and block potential attacks earlier in the threat chain.
If there is a real threat, the security team must mitigate the immediate issue and find and eliminate its root cause. They should also carry out a thorough investigation to determine how the threat got into the system, and look for solutions to prevent any future recurrence
The strength and effectiveness of a TDR program depends on the skills of its threat hunters and the capabilities of its tools. To protect the organization, TDR tools must accelerate threat detection and response. For this, the following features are vital:
A study in 2021 by Positive Technologies found that between 2018 and 2021, malware attacks increased by a staggering 137%. One reason for this increased proliferation is that malware is becoming more sophisticated, enabling it to evade traditional signature-based detection systems.
Conversely, TDR solutions use AI-based detection and sandbox-based content analysis that can identify this more sophisticated malware. They identify suspicious files by comparing the typical characteristics and behavior of malware against a newly discovered or existing file. If malware is detected, the tool automatically intervenes and safely quarantines the file. Even in-progress malware attacks can be identified and prevented.
Most modern organizations have diverse and complex IT infrastructure that leads to a wide attack surface. Threat actors may subsequently attack any system or application via many varied vectors. Effective TDR tools provide full visibility into the entire attack surface and utilize multi-layered threat detection techniques to discover any possible attack vector.
For TDR to be effective, it’s important to implement threat detection tools that generate high-quality alerts with very few false positives. Tools also should provide automated, playbook-based remediation workflows for common or known threats. Automation will enable security teams to coordinate their response and utilize their time more effectively.
A TDR solution should offer contextual threat intelligence in a user-friendly console. This can be used to reveal security blindspots and to correlate events between any enterprise resources that indicate brute force or account takeover attacks.
For a successful TDR program, a comprehensive and robust threat detection process should be the first step. For this, it’s important to first discover exactly what is at risk. All network assets must be discovered, logged and tracked so security personnel can better understand and protect their environment.
Further, to detect and respond to threats effectively, it’s important to perform regular vulnerability scanning and network traffic analysis (NTA). These processes can reveal any exploitable vulnerabilities and existing threats.
Deception technology is also recommended. This involves trapping intruders with strategically placed decoys or “honeypots.” When the attacker takes the bait, their actions are recorded and an alert is triggered. This enables security teams to observe the attempt and strengthen the organization’s predictive defenses accordingly.
An effective TDR program should deploy threat detection technology at every endpoint and to oversee the entire network. It’s generally best to implement a suite of integration-ready tools and these should:
Some other best practices include:
As the frequency and impact of cyberattacks increase, organizations need a way to react quickly to threats before it’s too late. Threat detection and response makes this possible. By using cutting-edge detection tools, contextual threat intelligence, and automated responses, enterprises can identify and respond faster to attacks and stay ahead of malicious cyber intruders and criminals.