
The security operations center (SOC) plays a critical role in any enterprise’s effort to protect its data from rapidly evolving cybersecurity threats.
However, for a variety of reasons revealed in the 2021 Devo SOC Performance ReportTM — which is based on the results of a survey of more than 1,000 security practitioners — organizations are frustrated with their SOC’s lack of effectiveness in performing its vital work. To combat the concerns the survey identified, SOCs need to refine how they operate. Here are four SOC best practices to help ensure enterprise success:
- Ensure the SOC has full visibility into data across the enterprise
- Create business alignment on the organization’s cybersecurity posture, while working to acquire executive commitment for sufficient funding and staffing of the SOC
- Build a highly interoperable, enterprise-wide security intelligence technology stack
- Make analyst retention a top priority
In this second post in our blog series revisiting key findings of the 2021 SOC Performance Report, we’ll dive into each of these SOC best practices and the challenges they address. The report also presents a new perspective on the challenges facing SOCs and the people who work in them by focusing on survey responses from SOC leaders and staff members.
SOC Best Practice #1: Ensure full visibility into enterprise data — and the cooperation of IT
64% of SOC leaders and 58% of SOC staff say turf or silo issues between the organization’s IT and security operations teams diminish the successful operation of the SOC, and 70% of SOC leaders and 58% of SOC staff say the lack of visibility into the IT security infrastructure is a big problem.
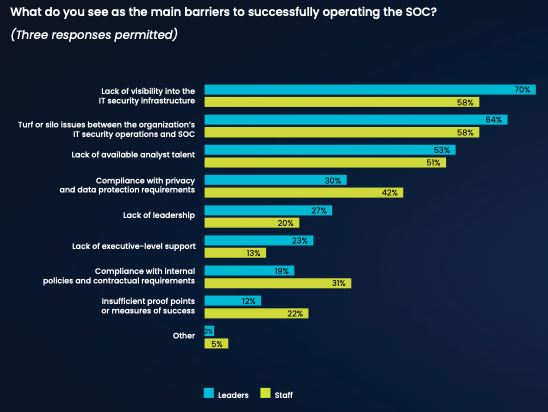
Organizations need to support and help increase their SOC teams’ effectiveness by creating stronger alignment between the SOC and security intelligence tools. With all of the challenges SOC analysts face, lack of access to the resources and information they need to do their jobs should not be one of them. In addition, turf or silo issues between IT security operations and the SOC must be addressed by empowered leaders who can facilitate information sharing and establish stronger collaboration between the teams.
SOC Best Practice #2: Create business alignment between the organization and the SOC
SOCs are not aligned with the objectives and needs of the business. Of those who are classified as high-performing SOCs, (those rated by survey respondents as a 9 or above on a 10-point scale measuring SOC effectiveness), only 32% of SOC leaders and 19% of respondents from low-performing SOCs say the objectives of the SOC are fully aligned with their organizations’ business needs. Nearly half of respondents from low-performing SOCs say they are not aligned at all. As a consequence, it is difficult to have senior leadership’s support and commitment to providing adequate funding for investments in technologies and staffing.
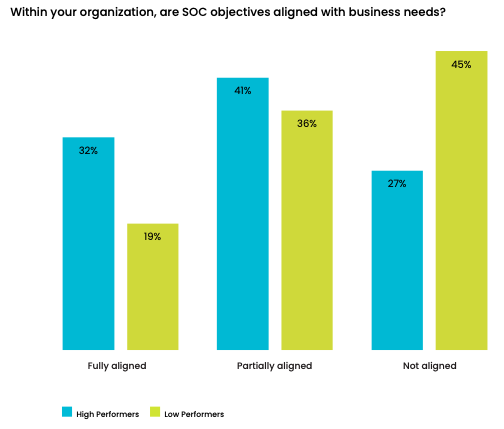
Given the crucial role SOCs perform for enterprises that are constantly barraged by sophisticated security threats, there’s no excuse for any misalignment between the SOC and the organizations’ objectives. If there are silos within an organization that stifle the necessary collaboration between the SOC team and other groups — especially IT security operations — it is incumbent upon leaders to break down those barriers. Doing so will create more strategic security processes and also likely will result in more budget money for the SOC, which will help it operate even more effectively.
SOC Best Practice #3: Make sure security tools and technologies are compatible throughout the enterprise
Only 46% of all respondents say their SOCs have high interoperability with their organizations’ security intelligence tools, and only 43% say their SOC effectively mitigates the risks after they are identified.
The responses epitomize what separates high- and low-performing SOCs, with the high responders consistently showing much more positive perceptions about how well they execute in several key areas. The high performers also exceed the responses of the overall survey right across the board.
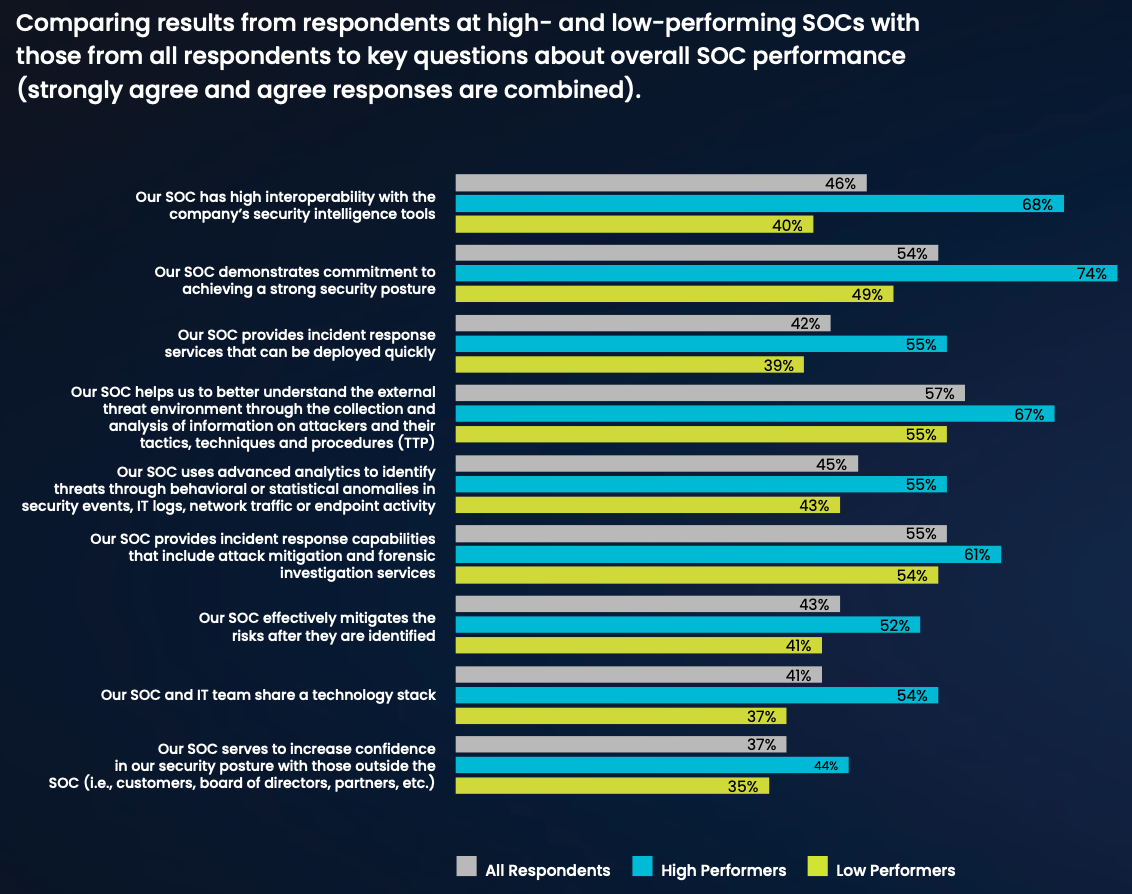
With all that’s at risk for any business that suffers a serious security breach, it’s inconceivable for the tools and technologies used to protect the enterprise and its data are not fully compatible and optimized throughout the organization. Few organizations have unlimited financial resources to throw at any problem. But spending whatever budget there is in a smart, efficient manner is a reasonable expectation. SOC teams must have the highest possible level of interoperability with the security intelligence tools being used elsewhere in the organization.
Again, the onus is on enterprise leaders and the heads of the affected teams to take the necessary steps to ensure there is openness and full collaboration. Security is not the place to take chances or allow turf wars to weaken what should be areas of strength.
SOC Best Practice #4: Make analyst retention a top priority
The challenge of working in a SOC makes it difficult to hire and retain experienced security analysts. 63% of respondents say it is very likely or likely that experienced SOC analysts would quit because of the stress of the job.
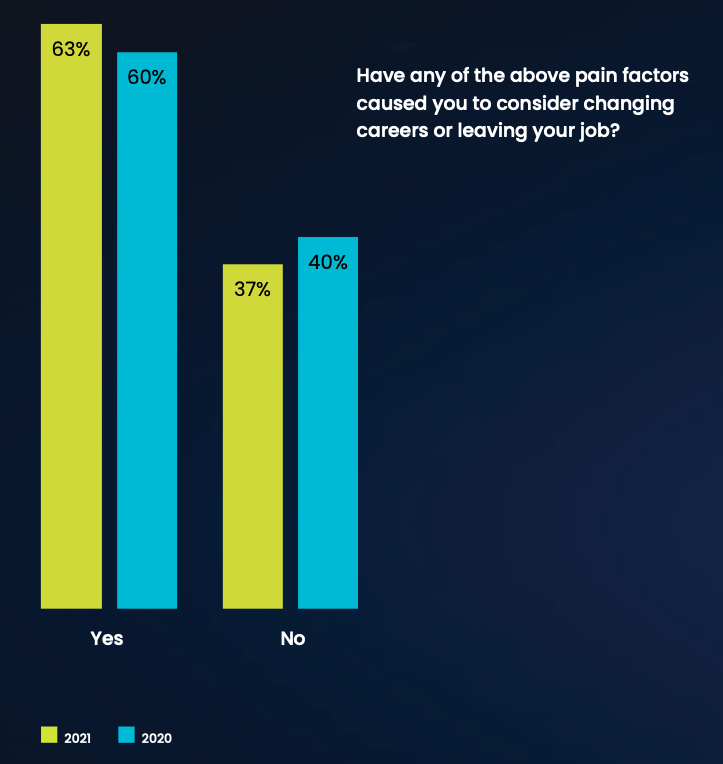
As for what makes working as a SOC analyst so painful, respondents identified many issues.
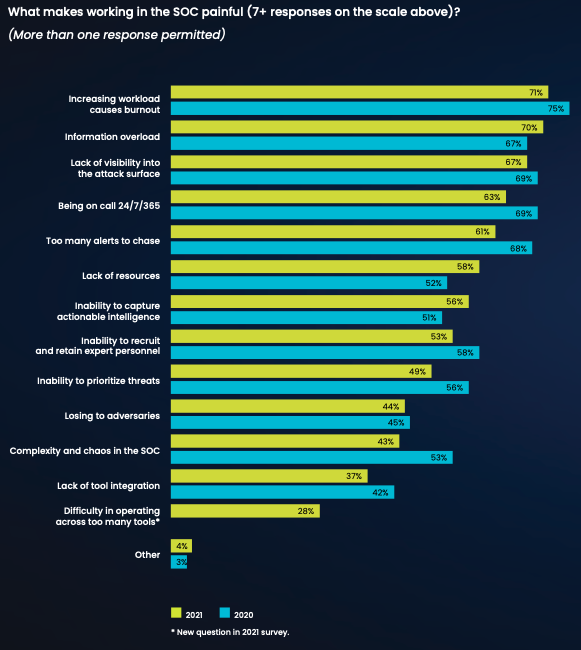
Leaders have a responsibility to reduce the stress and pain that come with working in a SOC. There is a significant shortage of skilled SOC analysts. Working conditions that drive those already in the field to leave the work they’ve been trained to perform must be improved. Without experienced, skilled SOC analysts, organizations will be unable to maintain, let alone enhance, overall enterprise security.
The best way to improve working conditions in the SOC, according to respondents, is to automate the analyst workflow. Other recommendations include normalizing the work schedule, giving analysts access to more out-of-the-box content, providing and more resources in general. No organization can have strong security without a strong, effective SOC.
There are many other valuable insights to be gleaned from this survey of professionals who deal with the challenges posed by today’s state of the SOC. Next up in our blog series: 4 Questions to Ask When Building a Security Operations Center.
Read the full 2021 Devo SOC Performance Report to learn more.




