
Building an in-house security operations center represents a significant commitment, both financially and strategically, to securing your enterprise.
According to the 2021 Devo SOC Performance ReportTM — which is based on the results of a survey of more than 1,000 security practitioners — 73% of respondents said their SOC was “very important” or “essential” to their organization’s overall cybersecurity strategy. Developing a complete and clear understanding of the key security operations center roles, responsibilities and disciplines is an essential foundation for building an effective SOC that will be an asset to the security of your business. Here are four of the most important questions to ask in building a security operations center:
- How should you structure your security operations team?
- If analyst retention is important to your organization, what training or tools do you provide?
- What technologies and services should a SOC have?
- How much does a security operations center cost?
In this, the third post in our blog series delving into our 2021 SOC performance report, we’ll examine methodologies for building an effective security operations center.
#1: How should you structure your security operations team?
Let’s start by answering the question “what is a SOC?” It’s a team of expert individuals and the facility in which they work to prevent, detect, analyze and respond to cybersecurity incidents. For a SOC to be successful requires support from the organization’s senior leaders, investment in the right technologies, and the ability to hire and retain a highly skilled and motivated team.
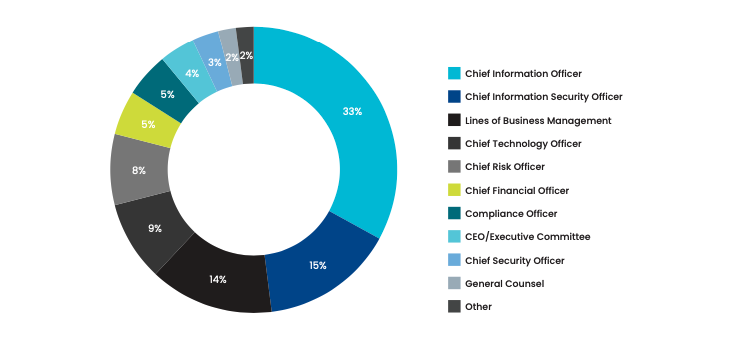
Most survey respondents said their CISO or CIO typically leads SOC operations. However, 15% say no single function has clear authority and accountability for the SOC. In these organizations, it can be much more difficult to make important decisions about SOC operations and how to improve performance.
Recommendation
When determining the reporting structure for your SOC, it is critical to select a leader who:
- Can create opportunities for each business unit to identify and prioritize strategic imperatives
- Can ensure the SOC team has full visibility into the organization’s IT environments
- Has sufficient clout within the business to ensure the SOC has sufficient budget to perform its vital work
#2: If analyst retention is important to your organization, what training or tools do you provide?
Analysts are the heartbeat of every SOC. However, those hearts are under constant pressure from myriad sources. And that’s beginning to take a toll. In fact, according to the 2021 SOC Performance Report, 63% of survey respondents said on-the-job pain in the SOC has caused them to consider changing careers or leaving their jobs.
On a 10-point scale, where 10 indicates SOC staff have a “very painful” experience performing their jobs, 72% of respondents rated the pain of SOC analysts at a 7 or above. That’s a bit lower than the 2020 number (78%), but it remains clear that working in a SOC continues to be far more painful than staff members and organizations can tolerate. This continuing high level of pain presents a wide range of challenges for SOC leaders, particularly when it comes to recruiting and, more importantly, retaining employees. And having an understaffed SOC or constant turnover of security talent can cripple an organization’s security posture.
So, how can SOC leaders anticipate, mitigate and even overcome these challenges? Additional questions from the survey for the 2021 report show SOC leaders favor options such as hands-on training courses or workshops, conferences or community events, tool-specific training, and more. The numbers in most categories remained largely consistent year over year.

Recommendation
Working in a SOC is a tough job, especially for the analysts who do the heavy lifting of identifying, hunting and investigating threats.
As these survey results indicate, SOC leaders said they provide hands-on training courses or workshops (62%), regular participation in conferences or community events (51%), and offer tool-specific training (45%) to reduce the turnover that increases cybersecurity vulnerability and leads to analyst burnout. As a result of providing access to these kinds of confidence-building opportunities, a more secure operations center is one step closer to reality.
#3: What technologies and services should a SOC have?
There is no shortage of technologies, tools, and services at the disposal of the modern SOC. Selecting the ones that are the best fit for your maturity and objectives are critical. Using the insights provided by survey respondents, below are the key recommendations to consider when your organization is ready to establish a SOC:
- Get your head in the cloud: More and more technologies are available as cloud solutions. Take advantage of this trend and maximize the flexibility and capabilities of your SOC by leveraging cloud-based SaaS offerings whenever possible. According to the report, 53% of respondents said the IT infrastructure that houses their SOC is mostly cloud (37%) or a combination of cloud and on-premises (27%). Just 27% of respondents said their infrastructure is mostly on-premises. This gap likely will continue to widen.
- Take advantage of threat intelligence: When asked to rate the importance of threat intelligence for threat detection, threat investigation, and threat hunting from a scale of 1=low importance to 10=extremely important, 71% of survey respondents rated it at least a seven or higher. However, just over a quarter of survey respondents (27%) said their companies are investing in threat intelligence while 50% would invest in it if related support and tools would be made available.
- Don’t overlook protection: The security solutions most often used by SOCs include firewalls (monitored or managed), intrusion-prevention systems (IPS), and intrusion-detection systems (IDS). Other frequently deployed solutions range from managed vulnerability scanning of everything from networks to applications, firewalls, and unified threat management (UTM) technologies.
- Be analytical: To accomplish the core SOC functions of detecting, hunting and responding to enterprise threats, most SOCs rely on a full stack of cybersecurity analytics These typically range from log management and SIEM to security orchestration and automation technologies. In 2021, 45% of survey respondents said their SOC uses advanced analytics to identify threats through behavioral or statistical anomalies in security events, IT logs, network traffic, or endpoint security.
#4: How much does a security operations center cost?
The average annual cybersecurity budget for organizations surveyed is $33 million. As shown in the following chart, only six% of respondents say more than 50% of the cybersecurity budget will be allocated to their SOC. The average allocation is 25% of the total cybersecurity budget. These numbers remained consistent year over year.

Recommendation
It’s not realistic to spend most of your cybersecurity budget on establishing and operating a SOC, but it’s not the place to pinch pennies, either. To be effective, SOCs require people, technology and other assets, all of which cost money. Building a SOC is a major commitment — financially and in terms of time and effort — for any business. That’s why business alignment on SOC objectives, budget usage, and performance measurement are so critical for ensuring strong business alignment moving forward. Make a plan and get buy-in from all involved groups and executive leaders. The goal is to achieve overall cybersecurity effectiveness. Make sure the SOC has the resources it needs to do its part.
There are many other valuable insights to be gleaned from this survey of professionals who must deal with the challenges posed by today’s state of the SOC. Next up in our blog series: 3 Use Cases to Reduce Analyst Burnout.
Read the 2021 Devo SOC Performance Report to learn more.




