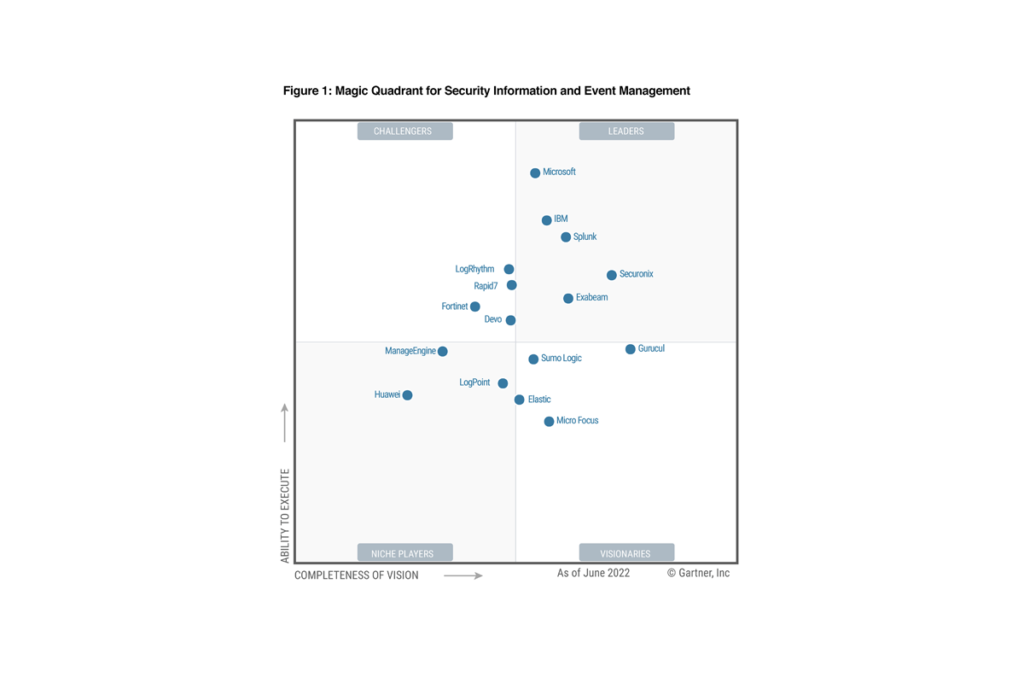
2022 Gartner® Magic Quadrant™ for SIEM
Unleash the power of your SOC with integrated SIEM, SOAR and UEBA.
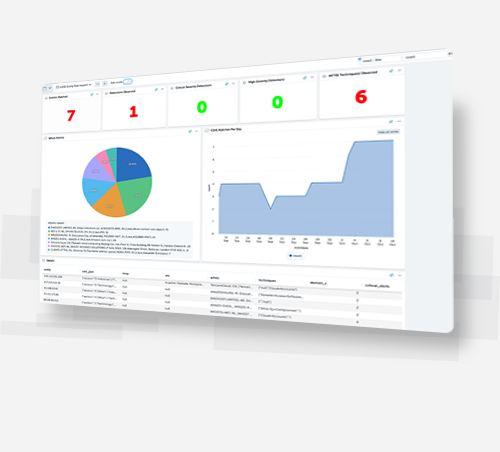
Intelligent SIEM continuously learns and improves its threat-handling accuracy, and scales effortlessly, to stay ahead of the growing SOC workload.
Autonomously investigate suspicious activity using attack-tracing AI.
Devo’s security-targeted AI is powered by our market-leading query performance and real-time data access to raw log data.
Devo Collective Defense securely analyzes alert data across the Devo community and identifies insights, trends, and Indicators of Compromise (IOCs) that are made available to Devo customers.