SOC analysts suffer from alert fatigue caused by too many data sources and platforms, too little context in investigations, too few people, and too little time. Mature cybersecurity teams manage this challenge by leveraging an integrated set of data analytics capabilities from best-of-breed solutions to establish an end-to-end experience — from data collection to response.
Analytics, informed by AI, allow for analyzing and enriching both traditional and non-traditional security data sources with context to extract meaningful, actionable insight. Next-gen security analytics solutions must combine a petabyte-scale data platform with advanced techniques, including machine learning and anomaly detection, to enable analysts to identify the threats that matter most to the business.
According to Gartner, by the end of 2024, 75% of enterprises will operationalize AI, driving a 5x increase in streaming data and analytics infrastructures. Moreover, AI capabilities are poised to augment analytics activities and enable companies to internalize data-driven decision-making. AI helps democratize data across the enterprise and saves data analysts, data scientists, engineers, and other data professionals from performing repetitive manual processes.
By applying analytics, SOC analysts can devote energy to investigating substantial threat incidents, events and vectors, reducing the probability of a successful attack, breach, theft or disruption of their enterprise. Having these capabilities in hand, with trained analysts to parse them to detect aberrant behavior or patterns, can be a game-changer for many organizations.
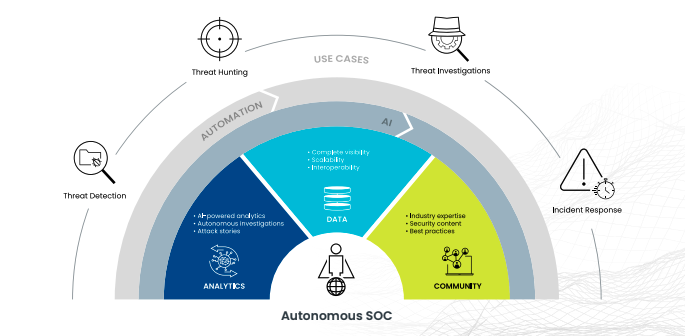
In this third post in our blog series introducing the journey to the autonomous SOC, we’ll discuss how analytics — when combined with automation — provide analysts with increased visibility into threats across on-premises and cloud environments. The combination helps accelerate incident response, from detection and triage to investigation and hunting.
Survey Says
According to the SANS Institute, almost 56% of organizations surveyed are “not satisfied” with the maturity of their analytics software. Barriers inhibiting adoption include a lack of trained and experienced staff, budget and time constraints, and the technical requirements to integrate cyber-threat intelligence.
Combining analytics with a SIEM enables enterprises to protect their investment in the latter while using analytics to unlock the rich log data stored by the former. This results in best practices for quickly detecting behavioral changes that identify threats. An analytics-driven SIEM also results in fewer data breaches, reduced patching costs, and lower compliance costs.
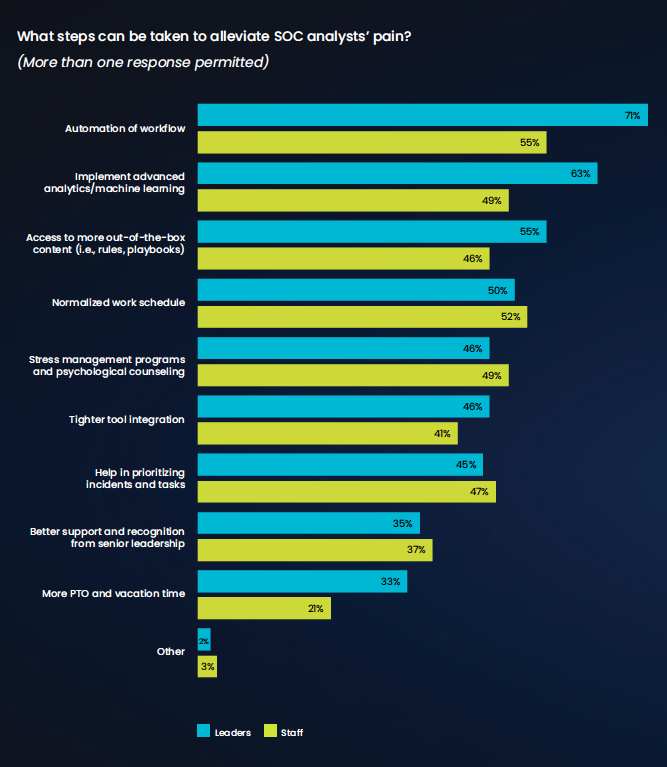
When it comes to the value of analytics in the modern SOC, the 2021 Devo SOC Performance ReportTM found that 63% of leaders surveyed believe implementing advanced analytics/machine learning would be a boon for reducing pain, an opinion shared by almost half of staff respondents, as well.
When SOCs can automate incident investigations and provide better context for alerts by filtering out noise, the volume of raw security alerts will decrease to a manageable number of concise, clearly categorized warnings.
More Benefits of Analytics
In the autonomous SOC, analytics also will provide analysts with increased visibility into threats across on-premises and cloud environments. This enhanced visibility will help SOC teams more efficiently manage security alerts and investigate compliance-based risks. The autonomous SOC will provide automated AI/ML-based analytics to empower analysts to perform incident response on large-scale, cloud-first infrastructures. These next-generation analytics will integrate seamlessly with security and IT tools to accelerate incident response, including detection, triage, investigation and hunting.
For next-gen SOCs, adopting analytics becomes a key element of a purpose-built cyber resilience strategy and moving an enterprise from mere prevention to true deterrence. They are also the best way to stem the rising tide of cyberattacks.
The next post in this series will discuss, we’ll discuss the third (and last) pillar of the autonomous SOC: community.
Ready to learn more about the autonomous SOC? Download the eBook.